#
Kerberoasting protections
_wald0 has a helpful tweet on preventing Kerberoasting. Also, this article from MS shares "a practical way to clean up dead SPNs in Active Directory," and authored a script to help in the cleanup efforts as well.
#
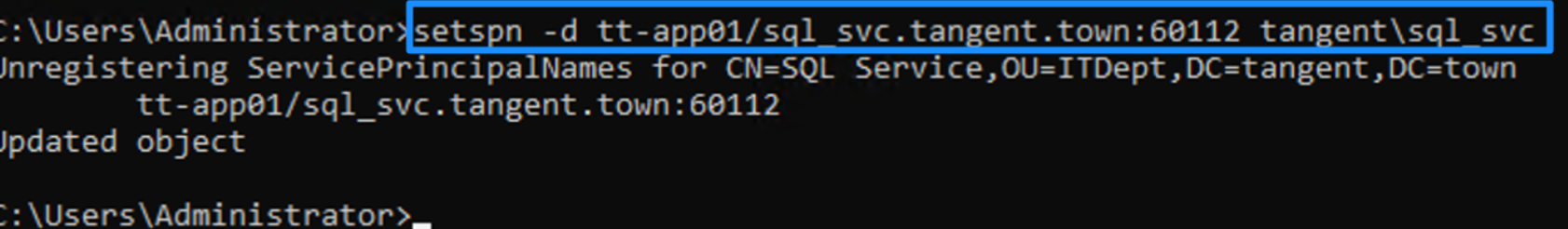
Running the cleanup script
Here's the script running in our test tangent.town environment:
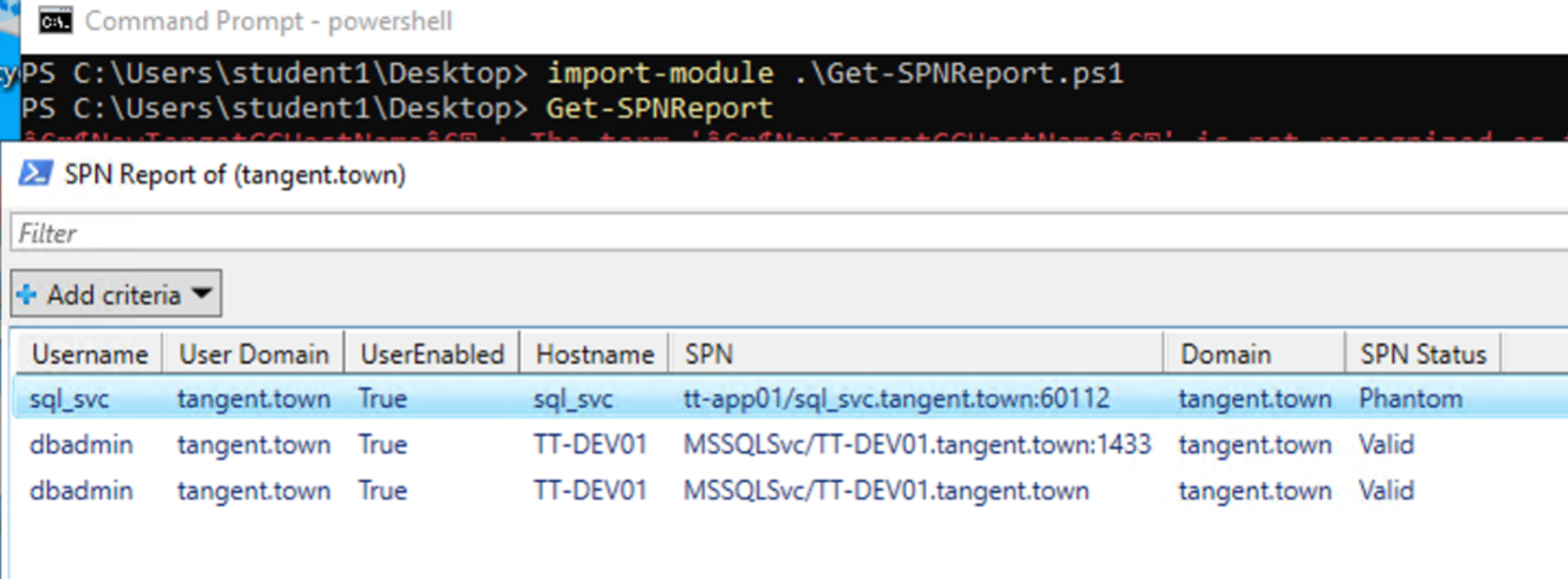
In my test environment, this script correctly identified my sql_svc account as being "phantom" because the SQL service had been uninstalled but the SPN wasn’t cleaned up. So now I can use the setspn command to do the final cleanup via this article: